The Importance of Red, Purple, and Blue Team Assessments in Cybersecurity
In today’s digital landscape, cybersecurity is more critical than ever. Organizations face a myriad of threats from cybercriminals, making it essential to adopt proactive measures to protect sensitive data and infrastructure. One of the most effective ways to achieve this is through Red, Purple, and Blue Team assessments. This blog post will delve into the significance of these assessments and how they can fortify your cybersecurity posture.
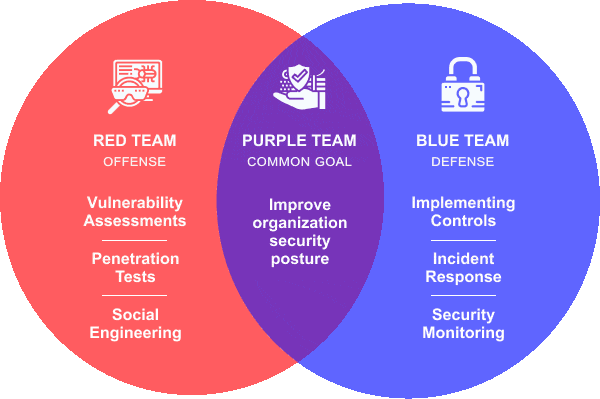
What Are Red, Purple, and Blue Team Assessments?
Before exploring their importance, it's essential to understand what Red, Purple, and Blue Team assessments entail:
- Red Team Assessments: These teams simulate real-world attacks to identify vulnerabilities in an organization’s defenses. They adopt the mindset of an adversary, using various tactics, techniques, and procedures (TTPs) to breach security measures.
- Blue Team Assessments: In contrast, Blue Teams are responsible for defending against these simulated attacks. They work to detect, respond to, and mitigate the threats posed by Red Teams.
- Purple Team Assessments: These teams serve as a bridge between Red and Blue Teams. They focus on collaboration, ensuring that insights from Red Team activities are effectively communicated to Blue Teams to enhance overall security.
Understanding these roles is crucial for appreciating the importance of Red, Purple, and Blue Team assessments in a comprehensive cybersecurity strategy.
1. Proactive Threat Identification
One of the primary benefits of Red, Purple, and Blue Team assessments is the proactive identification of vulnerabilities. By simulating attacks, Red Teams can uncover weaknesses before they are exploited by malicious actors. This proactive approach enables organizations to patch vulnerabilities and enhance security measures, significantly reducing the risk of data breaches.
2. Enhanced Incident Response
Blue Teams play a vital role in incident response, and their effectiveness is bolstered by insights gained from Red Team assessments. When Blue Teams understand the tactics used by Red Teams, they can develop better incident response strategies. Purple Teams facilitate this knowledge transfer, ensuring that lessons learned from simulated attacks are integrated into the organization’s defense protocols.
3. Continuous Improvement
Cybersecurity is not a one-time effort; it requires ongoing evaluation and improvement. Red, Purple, and Blue Team assessments create a cycle of continuous improvement. After each assessment, teams can analyze performance, identify gaps, and refine their strategies. This iterative process helps organizations adapt to evolving threats and maintain a robust security posture.
4. Realistic Training for Security Personnel
Training is a critical aspect of cybersecurity. Red, Purple, and Blue Team assessments provide realistic scenarios for training security personnel. By engaging in simulated attacks, team members can practice their response techniques in a controlled environment. This hands-on experience prepares them for real-world incidents and enhances their overall effectiveness.
5. Fostering Collaboration
Collaboration between teams is vital for a successful cybersecurity strategy. Red, Purple, and Blue Team assessments encourage communication and teamwork. Purple Teams play a crucial role in fostering this collaboration, helping to break down silos between Red and Blue Teams. This unified approach ensures that everyone is working toward the same goal: strengthening the organization’s defenses.
6. Compliance and Regulatory Requirements
Many industries have strict compliance and regulatory requirements regarding data security. Conducting Red, Purple, and Blue Team assessments can help organizations meet these requirements. By demonstrating that they have implemented robust security measures and regularly tested their effectiveness, organizations can ensure compliance and avoid potential penalties.
7. Increased Stakeholder Confidence
Investing in Red, Purple, and Blue Team assessments demonstrates a commitment to cybersecurity. This proactive approach can increase stakeholder confidence, including customers, partners, and investors. When stakeholders see that an organization is taking security seriously, it can enhance its reputation and build trust.
8. Cost-Effective Security Solutions
While investing in cybersecurity may seem costly, Red, Purple, and Blue Team assessments can lead to long-term savings. By identifying vulnerabilities early and addressing them before they can be exploited, organizations can avoid the substantial costs associated with data breaches. Additionally, these assessments help prioritize security investments, ensuring that resources are allocated effectively.
9. Customization of Security Strategies
Every organization is unique, with distinct challenges and requirements. Red, Purple, and Blue Team assessments allow organizations to tailor their security strategies to their specific needs. By analyzing the results of these assessments, organizations can identify which security measures are most effective and where adjustments are needed.
10. Preparing for the Future of Cybersecurity
The cyber threat landscape is constantly evolving, with new threats emerging regularly. Red, Purple, and Blue Team assessments help organizations stay ahead of the curve. By continually testing and refining their defenses, organizations can adapt to new attack vectors and technologies, ensuring they remain resilient against future threats.
Conclusion
The importance of Red, Purple, and Blue Team assessments in cybersecurity cannot be overstated. These assessments provide a proactive approach to threat identification, enhance incident response capabilities, foster collaboration, and support continuous improvement. By investing in these assessments, organizations can significantly strengthen their cybersecurity posture and better prepare for the challenges that lie ahead.
Incorporating Red, Purple, and Blue Team assessments into your cybersecurity strategy is not just a best practice; it is a necessity in today’s digital world. As cyber threats continue to evolve, so must our defenses. Embrace the power of these assessments and take a significant step toward securing your organization’s future.

Comments
Post a Comment